Welcome to IG Technologies
- Mon - Fri: 9.00 am - 5:00 pm
- Home
- About Us
- Solutions
- All-In-One Database Security
- Active Directory Security
- API Security Solution
- Application Security Solution
- Advanced Vulnerability Remediation
- Email Security Solution
- IT management
- MFA & IAM
- Mobile Device Management
- Online Banking Security
- Phishing Simulation & Cybersec Training
- Professional Services
- Protection for Microsoft 365
- Virtual Firewall
- XDR Platform All-in-One
- Request a Demo
- Become a Client
- Partners
All-in-One Database Security
Comprehensive Data Security
Elevating Security. Simplifying Governance.
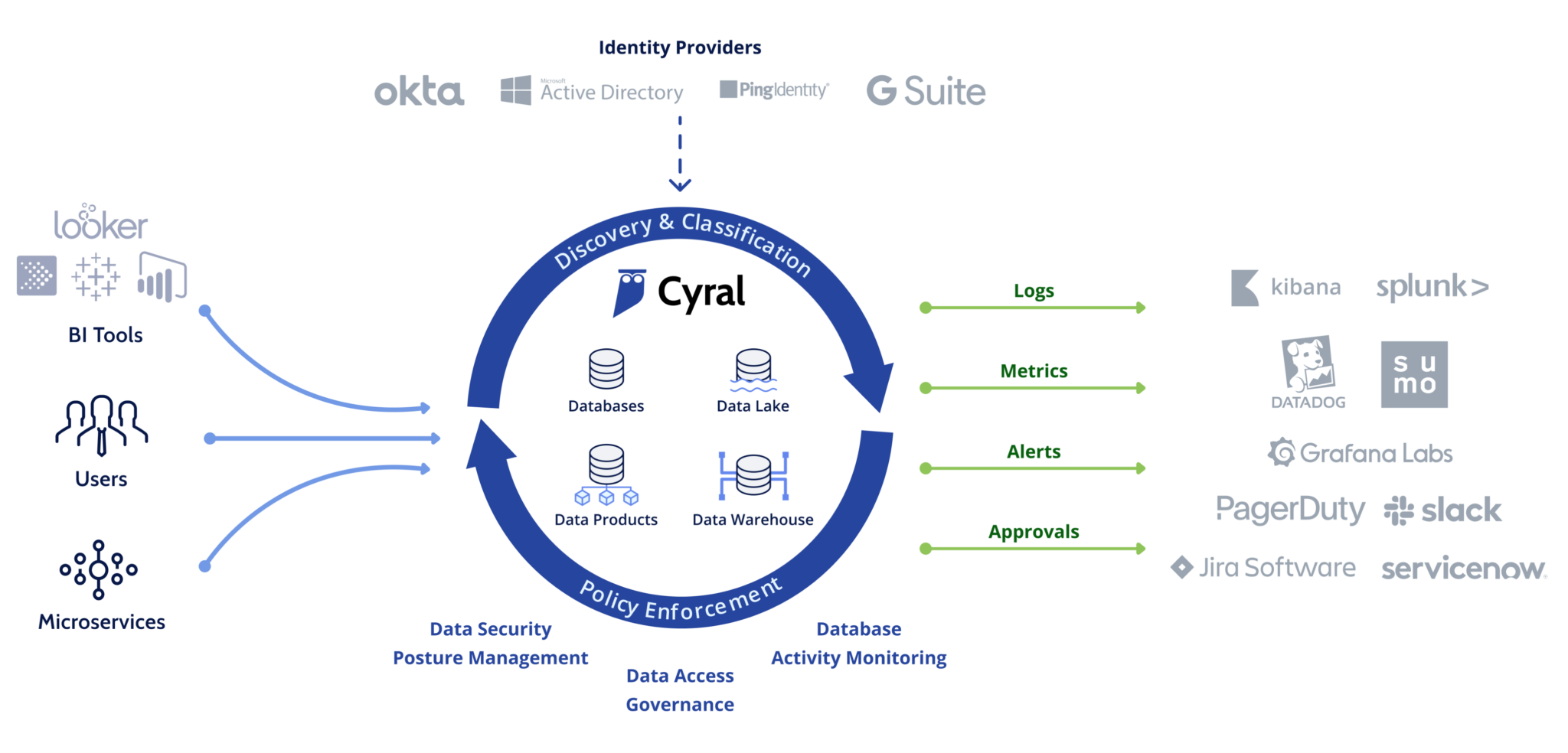
Secures All Databases and Data Lakes
Accurate data discovery and classification
Continuously scan your sensitive data stored across your entire environment, including cloud, SaaS, and data centers. The combination of sophisticated rule-based and AI classification achieves 99% accuracy at scale and provides deep risk and exposure analysis.
Automated remediation
Automatically remediate risky permissions, misconfigurations, ghost users, sharing links, and more. Varonis comes with ready-made remediation policies that can be customized for your organization.
Data-centric threat detection
Hundreds of expert-built threat detection policies automatically detect anomalies, alerting you to unusual file access activity, email send/receive actions, permissions changes, geo-hopping, and much more.
Enterprise ready
Varonis meets the needs of enterprise customers with world-class services, support for frameworks like RBAC, multi-tenancy, and industry standards, like FedRAMP, ISO/IEC, SOC, and HIPAA.
Powerful forensics layer
A powerful forensics layer aids investigations and compliance. It normalizes and enriches logs from your systems to create a searchable audit trail for answering data security questions.
Contact
Blog
Seller Profile Badge
© All right reserved 2025 by IG TECHNOLOGIES Privacy I Cookies I Terms and Conditions




